How I was able to Buy Tickets for 1 Rupee! — Payment Price Tampering
Hello everyone,

During my recent security hunting, I came across a business logic issue and yet simple vulnerability which was Payment price manipulation through which I could able to buy any number of Entry tickets and even adopt animals (Lion, Tiger) for months and years at 1 Rupee with the official owning Certificates.
I want to start by expressing my heartfelt gratitude to all of you for your overwhelming response and positive engagement with my previous blog post. For those who may have missed my previous writeup, I’ve included the link here for your convenience:
Summary :
This vulnerability is all about how I was able to book any number of entry tickets with just 1 Rupee with a simple vulnerability . Let me give you a good understanding of the target and it’s functionality.
Let’s say the target is target.com, it’s a ticket booking platform where you can book entry tickets. The target was having lots of different functionality including Animal Adoption, Animal Information, Visitors information, Profile Management, Tickets Booking with accessories etc.. So once after the ticket booking it is automatically generating a pdf invoice with all the booking information.
What is Parameter Tampering Vulnerability?
Parameter Tampering Vulnerability is a web-based attack intended as a business security threat that involves another party’s unauthorized manipulation and tampering with the website’s URL, web-page form or other parameters. It is manipulating the parameters exchanged between client and server in order to modify the application data such as user credentials, permissions, price, the quantity of products, etc.
The Tool I Used For This Finding :
Burpsuite
Steps to Reproduce:
First, Go to https://subdomain.target.com/ Enter the Joining details and Click on Create account, Now the user account will be created.
Navigate to subdomain.target.com/tickets/,Enter the Date and the Count of Adults, Children, infant count and cameras if needed and Click on Book Now Option.

The Total Amount is Calculated with +18 Internet Handling Charges as Well.
3.Total Payable Amount is 900+18 =918 for 10 Tickets. Now, Click on CONFIRM AND PAY NOW.

4. Capture this request using the Burp suite and Modify the Payment Request.

5.Change the amount=918 to amount=1, We have sucessfully Tampered the Amount. Here the main issue is even if we pay 1 rupee the invoice prints it as the original amount (ie.RS.918) .

6.Click Forward and Turn off the Intercept. And There we Goooooooooooo!
Now, Scan the QR and Pay rupee 1 and Booooooooooooooooooom !!!!!!
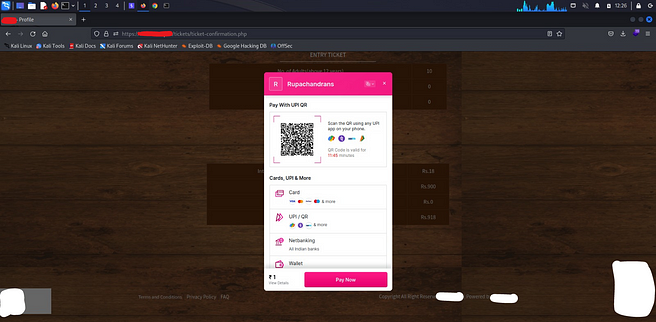
Proof Attached :
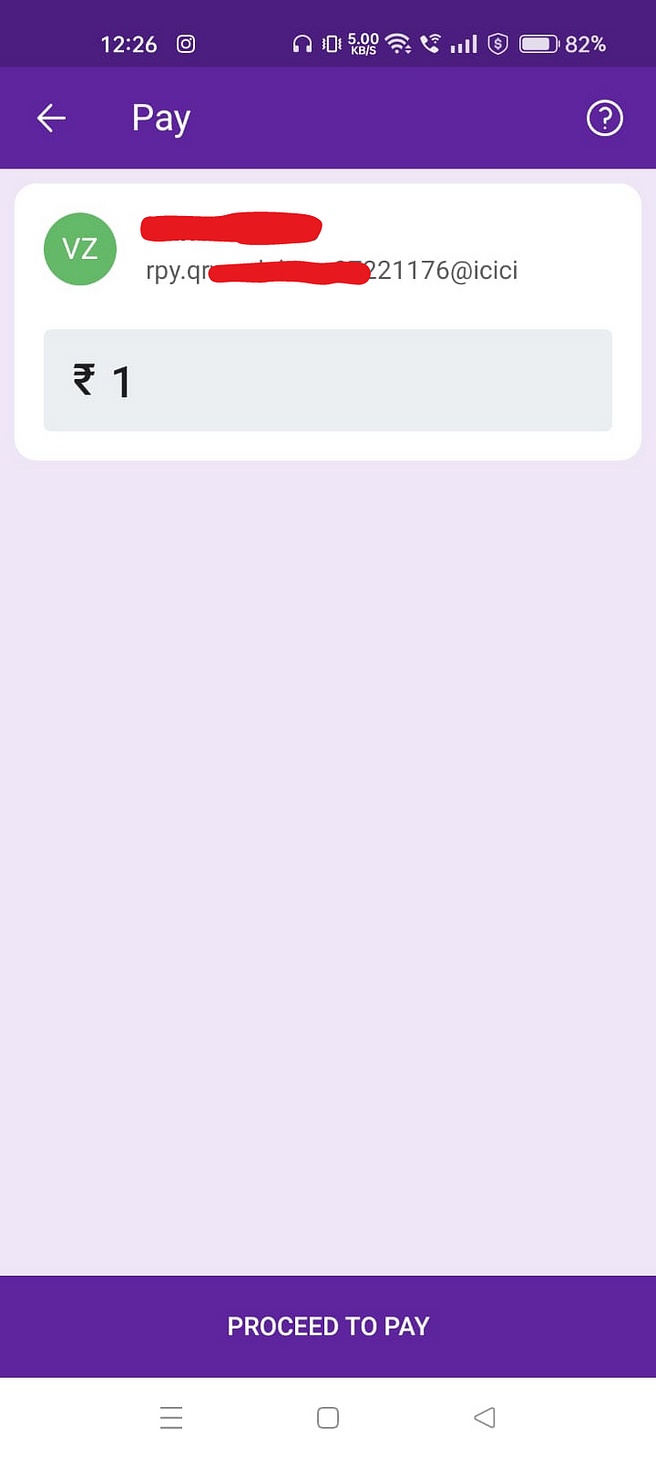
The payment was successfully and I paid just 1 INR for 918.00 INR with a simple Business Logic issue.
MITIGATION :
The price (parameters) should be validated on the server side. It also should use protections like cryptographic checksums. When tampered, the server should not process the request.
Payment Bypass is a type of parameter tampering attack where the manipulation of parameters exchanged between client and server is done in order to modify application data, such as user price, the quantity of product, etc. Imagine, you could buy a “Product” of Rs.1000 by just paying Rs 1.It’s a fortunate stroke of serendipity for the user but a huge financial loss for the business owners.
This blog post discusses mitigation techniques for parameter tampering in payment. The techniques discussed are for educational purposes only and should not be used to exploit vulnerabilities in real-world systems
Have a great day :)
Thanks, Regards
Rupachandran S
Available On :-
INSTAGRAM: https://www.instagram.com/gokulrupachandran/
TWITTER: https://twitter.com/RupachandranS
